Penetration Testing Methodology
Release: Version 1.1
Document
| Field | Description |
|---|---|
| Name | Penetration Testing methodology |
| Creators | Hacken OU |
| Subject | Pentest; security analysis; Web; Mobile; API; Network; attack vectors; |
| Description | This methodology defines the process for penetration testing and security assessments of blockchain-connected user interfaces and supporting infrastructure. It covers, but is not limited to, web and mobile interfaces for centralized and decentralized exchanges, wallets, mobile and desktop apps, gateways, APIs, and associated networks (cloud, on-premise, and hybrid). The methodology adopts an adversary-centric approach and details scoping, threat modelling, active testing (manual and automated), network and cloud configuration checks, exploit validation, and evidence-based reporting. It explains how Hacken OU will plan and execute audits of the target dApps and systems and provides stakeholders with clear preparation steps, success criteria, and expected deliverables for a thorough, repeatable assessment. |
| Author | Stephen Ajayi | dApp Audit Technical Lead at Hacken. |
| Date | October 15th, 2025 |
| Rights | Hacken OU |
Intro
In today's ever-evolving digital landscape, securing your organization's mobile, web, and network assets is crucial to safeguarding sensitive information from potential threats. Penetration testing serves as a vital component of comprehensive cybersecurity strategies, enabling organizations to proactively identify vulnerabilities and strengthen their defenses. This document outlines Hacken's approach for multi-cloud, mobile, web, and network penetration testing, providing a clear understanding of the benefits and outcomes these assessments aim to achieve.
During the information security assessment, the Hacken team focuses on the following goals and objectives:
- Identify technical and functional vulnerabilities.
- Estimate their severity level (ease of use, impact on information systems, etc.).
- Modeling the "most likely" attack vectors against the Customer's Information System.
- Proof of concept and exploitation of vulnerabilities.
- Draw up a prioritized list of recommendations to address identified weaknesses.
Alignment with International Standards
Hacken performs all audits and technical assessments in accordance with the NIST SP 800-115 – Technical Guide to Information Security Testing and Assessment and the Penetration Testing Execution Standard (PTES). These assets provide a structured foundation for planning, executing, and documenting technical evaluations such as vulnerability assessments, exploitation activities, and security code reviews. Hacken’s internal penetration testing methodology extends these principles to Web2 and Web3 environments to ensure consistency, repeatability, and verifiable outcomes.
Engagement Modes (Black / Grey / White Box)
These modes describe the level of access and internal context provided for the assessment.
They apply across Web applications, APIs, Mobile applications, and Network penetration tests.
Cloud is handled slightly differently in our model: we primarily perform cloud configuration reviews, which require broad read access and are therefore typically closer to a white-box engagement.
They generally do not change which vulnerability classes can exist; they change:
- Reachability: which attack paths/endpoints/flows can be exercised
- Depth: how far we can validate controls (roles, edge cases, internal-only functionality)
- Confidence: how conclusively we can validate intended vs actual security controls
In all modes, testing remains evidence-based and non-destructive by default. Any stress/abuse testing (e.g., rate limiting) is coordinated and time-boxed.
Quick comparison
| Mode | Access provided | Optimizes for | Typical outcome |
|---|---|---|---|
| Black-box | No credentials, minimal internal context | External attacker realism | Best for exposed attack surface + unauthenticated paths |
| Grey-box | Valid credentials and limited documentation | Practical depth & real user flows | Best balance of realism + coverage (most common) |
| White-box | Full documentation + credentials; optional source/config access | Maximum assurance | Best for regulated / high-value systems and strongest validation |
Black-box (no credentials, no internal knowledge)
What we do
- Enumerate externally exposed attack surface (applications, endpoints, services).
- Test unauthenticated paths and externally observable authentication mechanisms.
- Validate authorization controls where reachable.
- Perform input-focused testing where reachable (e.g., injection classes, unsafe input handling).
- Check abuse controls from an outside perspective (e.g., rate limiting) without impacting availability.
- Document information disclosure via responses, headers, and errors.
What we don’t do
- No source code review.
- No assumptions about intended internal behavior beyond what is externally observable.
- No validation of internal-only or undocumented functionality unless it is discoverable externally.
Grey-box (credentials + limited documentation)
Everything in black-box, plus:
- Authenticated user-flow testing.
- Role/permission boundary validation when roles are provided.
- Deeper authorization testing across objects/functions/tenants.
- Token/session lifecycle checks (refresh, revocation, reuse) where applicable.
- Business-logic abuse testing tied to real workflows/state transitions.
White-box (full documentation + credentials; optional code/config access)
Everything in grey-box, plus:
- Validate intended vs actual access control using documentation.
- Target edge-case/failure states that require internal context.
- Review available schemas/contracts (where applicable) for over-permissive fields and unintended data exposure.
- Optional (when in scope): focused source/config review of authN/authZ, validation, and access-control logic.
White-box does not mean “only code review”. Dynamic testing remains part of the approach unless explicitly excluded.
Security Assessment as Proactive Security
01 Web Penetration Testing: Safeguarding Your Digital Presence
Your web applications and APIs form the backbone of your organization’s digital presence, powering customer interactions, business operations, and data exchange. However, as technology evolves, so do cyber threats targeting these critical components.
Our comprehensive Web and API Penetration Testing methodology is designed to assess the security posture of both your web interfaces and backend services. Our team of ethical hackers methodically probes your systems to uncover vulnerabilities such as cross-site scripting (XSS), SQL injection, insecure direct object references (IDOR), authentication flaws, and API endpoint misconfigurations.
By simulating real-world attack scenarios, we expose weaknesses before adversaries can exploit them, ensuring your applications and APIs remain robust, compliant, and secure. The result is a resilient digital ecosystem that protects sensitive data, preserves business continuity, and safeguards your organization’s reputation.
02 Mobile Penetration Testing: Empowering Mobile Security
Your web applications are the face of your organization, serving as the primary channel for interacting with customers and conducting business. However, with the rise of sophisticated cyber threats, your web applications are increasingly vulnerable to attacks. Our Penetration Testing methodology is tailored to scrutinize the security posture of your web applications, leaving no stone unturned. Our team of ethical hackers expertly probes your web applications, meticulously identifying vulnerabilities such as cross-site scripting XSS, SQL injection, and session hijacking. By addressing these weaknesses, we ensure that your web applications remain resilient against malicious exploitation, securing your digital presence and safeguarding your organization's reputation.
03 Network Penetration Testing: Building a Resilient Infrastructure
The backbone of your organization's IT infrastructure, your network, requires vigilant protection against threats that could compromise its integrity. Our Network Penetration Testing services are designed to assess the robustness of your network architecture, identifying vulnerabilities that could be exploited to gain unauthorized access. Our experienced team performs comprehensive testing, examining cloud and on-premise network devices, firewalls, routers, and switches, to evaluate their resilience against attacks. By deploying cutting-edge methodologies, we strengthen your network security, ensuring your critical assets are shielded from unauthorized access, data breaches, and network intrusions.
Fundament of Hacken's Security Assessment
Our Security Assessment approach grew out of the combination of industry recognized best practices and highest team members individual skills
01 Used Best Practices and International Standards:
- PCI DSS
- NIST SP 800115 Technical Guide to Information Security Testing and Assessment
- OWASP
- OWASP Top 10
- OWASP ASVS
- OWASP MASVS
- OWASP Mobile Security Testing Guide MSTG
- OWASP WSTG
- PTES Penetration Testing Execution Standard
- MITRE ATT&CK
- SANS
- SANS Conducting a Penetration Test on an Organization
- SANS Network Application Security Assessment and Ethical Hacking
- SANS Top-25 CWE
- The Open Source Security Testing Methodology Manual
02 Hacken's Team Individual Skills:
- Offensive Security certified:
- Offensive Security Certified Professional
- Offensive Security Experienced Penetration Tester
- Offensive Security Web Assessor
- Offensive Security Web Expert
- Offensive Security Wireless Professional
- Offensive Security Exploit Developer
- Offensive Security Certified Expert 3
- Zeropoint Security certified:
- Certified Red Team Operator
- Certified Red Team Lead
- CREST Qualified Consultants:
- CREST Practitioner Security Analyst
- CREST Registered Penetration Tester
- eLearnSecurity:
- eWPTXv2 Web Penetration Tester eXtreme
- PTXv2 Penetration Tester Extreme
- Pentester Academy(Altered Security):
- Certified Azure Web Application Security Professional CAWASP
- Pentester Academy DevSecOps Professional
- Cloud Security Professional PACSP
- Certified Red Team Expert CRTE
- Certified Az Red Team Professional
- Certified Red Team Professional CRTP
- HackTheBox cloud pro labs certifications:
- Cloud Security Specialist: GCP offensive Blizzard
- Cloud Security Specialist: Azure offensive Cyclone
- Cloud Security Specialist: AWS offensive Hailstorm
- Certified DevSecops Professional (CDP)
03 Based Security Assessment Team Composition
| # | Team Member and Role | Components to review |
|---|---|---|
| 1 | Lead Penetration Tester | Project planning and executing Penetration Testing Identify security and business risks for application Preparing artifacts and deliverables Results Presentation |
| 2 | Penetration Tester | Penetration Testing Identify security and business risks for infrastructure |
| 3 | Delivery Manager | Customer communication Project delivery and quality control |
04 Security Assessment Approach
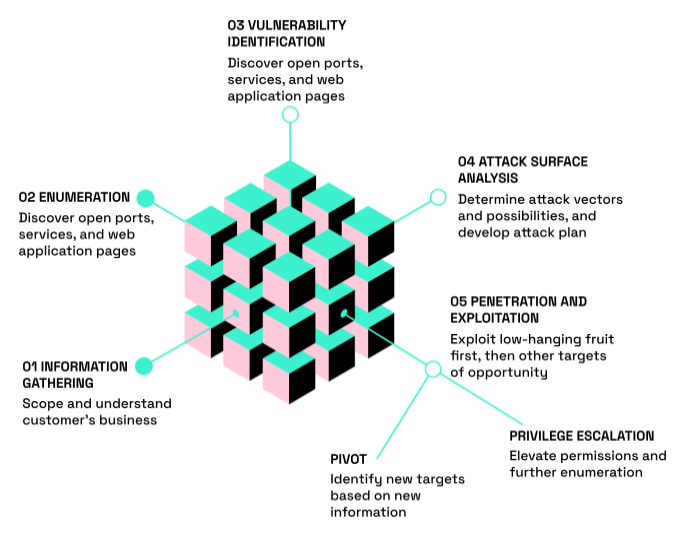
05. Threat Modeling & Attack Surface Analysis
Purpose
Threat modeling identifies potential adversaries, attack paths, and the most likely exploitation scenarios targeting the client’s systems. It ensures vulnerabilities discovered during testing are contextualized within real-world threats and mapped to relevant attacker techniques, enabling risk-driven remediation.
Approach
Hacken follows a combined methodology, integrating PTES Threat Modeling, NIST SP 800-115 risk assessment, and industry-standard frameworks (MITRE ATT&CK, STRIDE, PASTA, CWE).
1. Adversary Profiling
- Define attacker categories (script kiddie, insider threat, cybercriminal, APT/state actor).
- Model likely attacker goals: data theft, service disruption, lateral movement, financial fraud, reputational damage.
- Consider attacker capabilities (tooling, access level, persistence).
2. Asset & Attack Surface Identification
- Enumerate in-scope assets: cloud services, APIs, web/mobile applications, endpoints, network infrastructure.
- Map exposure levels: external-facing, internal-only, privileged, or safety-critical.
- Document trust boundaries (user ↔ application, app ↔ database, tenant ↔ cloud provider).
3. Threat Modeling Frameworks
- STRIDE – Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege.
- PASTA – Process for Attack Simulation & Threat Analysis, aligning with business impact and compliance risk.
- MITRE ATT&CK – Each exploitation path mapped to ATT&CK techniques and tactics.
- CWE/SANS Top 25 – Findings mapped to weakness IDs for developer remediation.
4. Attack Path Simulation
- Construct “most likely” attack vectors using intelligence gathered during reconnaissance.
- Analyze chaining of vulnerabilities (low → medium → privilege escalation).
- Document lateral movement opportunities (pivoting via compromised credentials or misconfigurations).
- Model potential business impact (loss of confidentiality, availability disruption, safety impacts).
5. Prioritization & Reporting
Every vulnerability in the Security Assessment Report includes:
- CVSS v4.0 score – Technical severity.
- CWE mapping – Development weakness reference.
- Business Impact Assessment – Based on environmental metrics and threat model.
Findings are prioritized by combining CVSS v4.0 severity, exploitability, attacker profile, and business/safety impact.
Outcome
Threat Modeling & Attack Surface Analysis ensures Hacken’s penetration tests provide actionable intelligence, not just raw vulnerability lists.
By correlating technical findings with adversary behaviors and organizational risk, remediation efforts are prioritized to address the most impactful and exploitable weaknesses first.
06 Based Security Assessment Tools Kit
The Hacken team utilizes automated tools along with manual methods to identify security vulnerabilities and perform tests to actively exploit them in a non-harmful manner. It's important to note that the choice of tool depends largely on the specific needs of the pen test.
The below list only scratches the surface of the variety of tools available to penetration testers. Depending on the specifics of a test, the scope of the project and the technological details of the target, a wide range of other specialized tools may also be used. From open source scripts to commercial tools, the field of penetration testing is dynamic and rapidly evolving, always adapting to meet the challenges posed by the ever-changing landscape of cybersecurity.
General
| Tool Name | Description | Applicable Stages |
|---|---|---|
| Kali Linux | A free and open-source Linux-based operating system that's often used by cybersecurity professionals for various forms of penetration testing, ethical hacking, and network security assessments. It's developed, maintained, and funded by Offensive Security, a provider of information security training and penetration testing services. | All-stages Tool |
| Metasploit | An exploitation framework used to compile and execute exploit code against vulnerable systems | All-stages Tool |
| HashCat | is a well-known password cracking tool that's favored for its versatility and speed. It's an open-source tool often used by penetration testers and cybersecurity professionals to recover (or "crack") a variety of hashed passwords. | Exploitation |
| BloodHound | an open-source tool that uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment | Vulnerability Identification Attack Surface Analysis Enumeration |
Multi-Cloud Penetration Testing
| Tool Name | Description | Applicable Stages |
|---|---|---|
| ScoutSuite | An open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments. Using the APIs exposed by cloud providers, Scout Suite gathers configuration data for manual inspection and highlights risk areas. | Whitebox Enumeration Vulnerability Identification |
| CloudFox | An open source command line tool created to help penetration testers and other offensive security professionals find exploitable attack paths in cloud infrastructure. | Whitebox Enumeration |
| awspx | A graph-based tool for visualizing effective access and resource relationships within AWS. It resolves policy information to determine what actions affect which resources, while taking into account how these actions may be combined to produce attack paths. | Whitebox Enumeration |
| cloud_enum | A multi-cloud OSINT tool. Enumerate public resources in AWS, Azure, and Google Cloud. | Whitebox Enumeration |
| AzureHound | The BloodHound data collector for Microsoft Azure. | Whitebox Enumeration |
| Powler | An open source security tool to perform AWS, GCP and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. | Whitebox Enumeration |
| MicroBurst | An open source security tool includes functions and scripts that support Azure Services discovery, weak configuration auditing, and post exploitation actions such as credential dumping. | Whitebox Enumeration Vulnerability Identification |
| AWS pwn | A collection of pre-written scripts for performing various tasks related to penetration testing AWS. | Whitebox Enumeration Vulnerability Identification |
Web Application
| Tool Name | Description | Applicable Stages |
|---|---|---|
| Burp Suite Pro | A leading toolkit for web security testing. Developed by PortSwigger, this software provides a platform for performing security testing of web applications. It is used by penetration testers, cybersecurity professionals, and ethical hackers to identify potential vulnerabilities in web applications. | Vulnerability Identification Attack Surface Analysis Penetration And Exploitation |
| Nuclei | An open-source project that provides fast and customizable vulnerability scanning based on templated workflows. It's commonly used in penetration testing and bug bounty hunting. Developed by the team at ProjectDiscovery.io, Nuclei is designed to be highly flexible and can be tailored to work with a wide variety of network protocols and infrastructure. | Vulnerability Identification |
| ffuf | An open-source, fast web fuzzer written in Go. A fuzzer is a tool used in testing and it works by feeding a wide range of inputs into a program to see if any of them cause it to behave in an unexpected or unintended way | Penetration And Exploitation |
| SQLMap | is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. | Vulnerability Identification Exploitation |
| TmplMap | is a tool that automates the process of detecting and exploiting Server-side Template Injection vulnerabilities SSTI. | Vulnerability Identification Exploitation |
| SSRFMap | is an open-source penetration testing tool used to automate the process of detecting and exploiting SSRF vulnerabilities | Vulnerability Identification Exploitation |
| Acunetix | A web vulnerability scanner designed to identify security issues in web applications. Developed by Acunetix Ltd., it's primarily used by security analysts and developers to scan websites and web applications for potential vulnerabilities such as SQL Injection, Cross-Site Scripting XSS, Cross-Site Request Forgery CSRF, and others. | Vulnerability Identification |
| WPscan, JoomScan, DroopeScan | The open-source common CMS security testing tools. | Vulnerability Identification |
Mobile
| Tool Name | Description | Applicable Stages |
|---|---|---|
| MobSF | is an open-source, automated mobile app security testing framework. It is designed to help security researchers, developers, and penetration testers assess the security of mobile applications on various platforms, including Android and iOS. | Penetration And Exploitation Attack Surface Analysis |
| Objection | is an open-source runtime mobile exploration framework developed by SensePost. It is designed to assist security researchers and mobile app developers in analyzing and manipulating the behavior of Android and iOS apps during runtime. | Penetration And Exploitation Attack Surface Analysis |
| Frida | is a free and open source dynamic code instrumentation toolkit written by Ole André Vadla Ravnås that works by injecting the JavaScript engine (previously and ) into the instrumented process. Frida lets you execute snippets of JavaScript into native apps on Android and iOS (as well as on ). | Penetration And Exploitation Attack Surface Analysis |
| Passionfruit | is an open-source iOS application analysis tool developed by the team at the University of California, Santa Barbara UCSB. It is designed to assist security researchers and developers in analyzing the runtime behavior of iOS applications and identifying potential security issues. | Attack Surface Analysis Vulnerability Identification Enumeration |
| SSL Kill Switch 2 | Blackbox tool to disable SSL certificate validation - including certificate pinning - within iOS and macOS | Exploitation |
Network
| Tool Name | Description | Applicable Stages |
|---|---|---|
| Nmap | An open-source port scanner and service enumeration tool used for mapping networks, systems, and services. | - Enumeration |
| Nessus | is a remote security scanning tool that scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network. | - Enumeration - Information Gathering - Attack Surface Analysis |
| amass | A powerful open-source tool used for information gathering, specifically for discovering subdomains associated with a given domain. It was developed by OWASP Open Web Application Security Project, a well-known nonprofit that works to improve the security of software. | - Information Gathering |
| CloudEnum | CloudEnum is an open-source tool developed by Chris Moberly, a researcher from the Australian security company Assetnote. The tool is designed to help penetration testers and security researchers enumerate publicly exposed cloud resources. | - Enumeration - Attack Surface Analysis |
| MicroBurst | A collection of PowerShell scripts that are used for assessing and exploiting security vulnerabilities in Microsoft's Azure cloud. These scripts were developed by NetSPI, a security consulting company. | - Penetration And Exploitation - Enumeration |
| CredMaster | An open-source util for password spray attack via Amazon AWS passthrough proxies, shifting the requesting IP address for every authentication attempt. This dynamically creates FireProx APIs for more evasive password sprays. | - Penetration And Exploitation |
| Wireshark | is a widely-used, open-source network protocol analyzer and packet capture tool. It allows users to analyze network traffic in real-time and examine captured packets to understand and troubleshoot network issues. | - Enumeration |
| Impacket | is an open-source collection of Python classes developed by SecureAuth Corporation for working with network protocols. Impacket is highly effective when dealing with Windows systems, given its focus on Microsoft's SMB Server Message Block, MSRPC Microsoft Remote Procedure Call, and other protocols. | - Penetration And Exploitation - Pivot - Privilege Escalation |
| Rubeus | is a sophisticated tool used by penetration testers and red teamers to interact with Microsoft's Kerberos protocol. | - Penetration And Exploitation - Pivot - Privilege Escalation |
| CrackMapExec | often abbreviated as CME, is a popular open-source tool in the cybersecurity community. It's used for testing the security of Microsoft's Active Directory environments and is widely used by penetration testers and red teamers during the reconnaissance phase of an operation | - Penetration And Exploitation - Pivot - Privilege Escalation |
07. Severity Scoring Scale
The severity level (criticality level) of each vulnerability is determined using the Common Vulnerability Scoring System version 4.0 (CVSS v4.0) combined with organization-specific business impact.
CVSS v4.0 provides enhanced base, threat, and environmental metrics that better reflect modern exploitation patterns, recovery characteristics, and safety impacts.
CVSS v4.0 Overview
We use CVSS v4.0 to calculate a standardized numerical score for every technical vulnerability.
The score is computed using three metric groups:
1. Base Metrics (intrinsic to the vulnerability)
- Attack Vector (AV) — Network (N), Adjacent (A), Local (L), Physical (P).
- Attack Complexity (AC) — Low (L), High (H).
- Attack Requirements (AT) — None (N), Present (P) — conditions that increase difficulty beyond complexity.
- Privileges Required (PR) — None (N), Low (L), High (H).
- User Interaction (UI) — None (N), Required (R).
- Confidentiality (VC), Integrity (VI), Availability (VA) — None (N), Low (L), High (H).
- Safety (SC, SI, SA) — New v4.0 metrics that measure potential harm to human safety or physical processes.
2. Threat Metrics (real-world exploitability & actor capability)
- Exploit Maturity (E) — Not Known / Proof-of-Concept / Functional / High.
- Automatable (AU) — Whether the exploit can be automated or weaponized at scale.
- Recovery (R) — The expected effort/time to recover affected systems after exploitation.
3. Environmental Metrics (contextual modifiers)
- Modified Base Metrics (e.g., MAV, MAC, MPR, etc.) — Adjust base values to reflect compensating controls.
- Confidentiality/Integrity/Availability Requirements (CR/IR/AR) — How important each property is to the organization.
- Safety Requirement (SR) — Importance of safety impact for the organization.
Severity Rating Mapping
We map CVSS v4.0 numeric output to severity categories used throughout our reports:
| Severity | Score Range |
|---|---|
| Informational | 0.0 |
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
How Hacken Applies CVSS v4.0
- Base Score – Calculated per CVSS v4.0 guidelines and included in every technical finding.
- Threat Factors – Findings include exploit maturity and automatable indicators to reflect near-term risk.
- Where public exploits or active campaigns exist, threat metrics increase remediation urgency.
- Environmental Rescoring – For client-specific reports, a contextual rescore adjusts the base score for business-critical systems, compensating controls, or safety impacts.
- The rescored value and rationale are documented.
- Rescoring on Retest – After remediation, findings are rescored using CVSS v4.0 in the retest report to reflect residual risk.
- Standards Mapping – Each finding includes mappings to CWE (developer remediation), CVE (if applicable), and MITRE ATT&CK technique(s) (threat-modeling context).
Proof-of-Concept (PoC) & Prioritization
- Proof-of-Concept (PoC) – Provided for each Medium, High, and Critical finding.
- Prioritization Guidance – Combines:
- CVSS v4.0 score
- Exploit availability (Threat metrics)
- Business impact (Environmental metrics)
- Regulatory/compliance implications (e.g., PCI, HIPAA, GDPR)
Deliverables
The main deliverable of the Security Assessment project is the Security Assessment Report including:
- Security Assessment Scope
- Team Composition
- Main Attack&Threat Vectors
- Goals and objectives
- Summary of Findings
- Remediation Check Protocol
- Key Findings
- Web/Mobile/Network Specific Vulnerabilities
Disclaimer
The conducted Security Assessment is valid on the date of the report submission. The description of findings, recommendations, and risks was valid on the date of submission of the report. Any projection to the future of the report's information is subject to risk due to changes in the Infrastructure architecture, and it may no longer reflect its logic and controls.
Stay in Touch
We’re excited to share our expertise and help you build a safer web3 future. If you have any questions, feel free to contact us.